The log4j vulnerability parses this and reaches out to the malicious host via the Java Naming and Directory Interface JNDI. Similarly to other high-profile vulnerabilities.
The vulnerability also impacts Adobe ColdFusion.

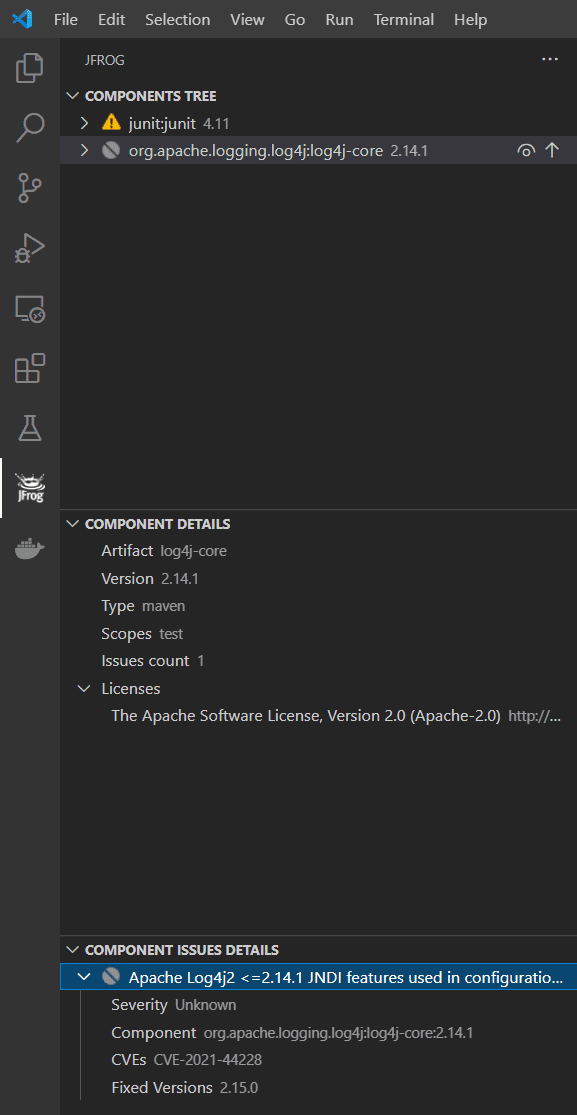
Log4j vulnerability jar. These are the sorts of vulnerabilities that could be. On December 10 2021 a security vulnerability was identified in Apache Log4j 2 version 2141 or earlier CVE-2021-44228. CVE-2021-44228 is a remote code execution RCE vulnerability in Apache Log4j 2.
Pega software can use the Log4j component in two. Reports of a Minecraft log4j exploit have surfaced with players sharing how to fix the vulnerability of java versions 17 to 118. A new critical remote code execution vulnerability in Apache Log4j2 a Java-based logging tool is being tracked as CVE-2021-44228.
This gives an attacker the ability to run any code they would like on the target the. Adobe is investigating any potential impact and is taking action including updating affected systems to the latest versions of Apache Log4j recommended by the. Yesterday the Apache Foundation released an emergency update for a critical zero-day vulnerability in Log4j a ubiquitous logging tool included in almost every Java application.
As it was vulnerable to illegitimate access by bad actors and hackers it is being anticipated that it might have been used to access data. There is a critical security vulnerability CVE-2021-44228 in the Log4j which is a popular logging library for Java-based applications. The Apache Logging Services team provides the following mitigation advice.
Threat actors are actively weaponizing unpatched servers affected by the newly identified Log4Shell vulnerability in Log4j to install cryptocurrency miners Cobalt Strike and recruit the devices into a botnet even as telemetry. The bug makes several online systems built on Java vulnerable to zero-day attacks. The vulnerability affects multiple versions of Log4j 2.
This vulnerability was discovered by Chen Zhaojun of Alibaba Cloud Security Team. Log4j versions 20 through 2141 have been found to be vulnerable to a Remote Code Execution vulnerability due to the fact JNDI does not protect against attacker-controlled directory service providers. Yesterday December 9 2021 a very serious vulnerability in the popular Java-based logging package Log4j was disclosed.
A so-called Remote Code Execution RCE. The crafted request uses a Java Naming and Directory Interface JNDI injection via a variety of services including. 10 CVE-2021-44228 in the Apache Log4j logging software.
The vulnerability was discovered by Chen Zhaojun from Alibabas Cloud Security team. To build a custom vulnerability detection rule open Prisma Cloud and navigate to the following page. This was designed to make a JNDI call to substitute some information from a remote resource if a particular format of the log was found.
CVE-2021-44228 also identified as Log4Shell is a critically rated vulnerability impacting Log4j 2 Java log manager which is integrated into Apaches web server suite. The issue has been. What is Log4J vulnerability.
Apache Log4j is part of the Apache Logging Project. December 12 2021 Ravie Lakshmanan. Description of the CVE-2021-44228 vulnerability.
The Log4j JAR can be directly included in our project or it can be hidden away in one of the dependencies we include. The Log4j software is ubiquitously used by most organizations around the world. If your organization deploys or uses Java applications or hardware running Log4j 2x your organization is likely affected.
The recent vulnerability is identified and affected on the 2x version of log4j primarily. An unauthenticated remote attacker could exploit this flaw by sending a specially crafted request to a server running a vulnerable version of log4j. Due to this deployment methodology the impact is difficult to quantify.
Apache Log4j Vulnerability Log4Shell Widely Under Active Attack. For example using Syft to. Because of the widespread use of Java and log4j this is likely one of the most serious vulnerabilities on the Internet since both.
By and large usage of this library is one of the easiest ways to log errors and that is why most Java developers use it. Additionally Prisma Cloud users can also build a custom vulnerability detection rule to identify if any system is running a vulnerable Log4j package or JAR file with a version equal to or older than 2141. Remediating the Log4J Vulnerability.
10 Dec 2021 350 pm. Typical CVE-2021-44228 Exploitation Attack Pattern. This issue was fixed in Log4J v2150.
The Log4j 2 library is very frequently used in enterprise Java software. This vulnerability poses a risk to private data and the availability of your web server. In previous releases 210 this behavior can be mitigated by setting system property log4j2formatMsgNoLookups to true or by removing the JndiLookup class from the classpath example.
This vulnerability could allow malicious actors to take control of organizational networks using Log4j. Log4ShellThis vulnerability within the popular Java logging framework was published as CVE-2021-44228 categorized as Critical with a CVSS score of 10 the highest score possible. A zero-day vulnerability was identified on Friday Dec.
Analysis and Remediation Guidance to the Log4j Zero-Day RCE CVE-2021-44228 Vulnerability. If it is exploited by bad actors it will allow remote. Mitigating the Apache Log4j 2 Vulnerability.
Staying Secure Apache Log4j Vulnerability. Zip -q -d log4j-core. Log4j is a Java package that is located in the Java logging systems.
A vulnerability rated with a Critical impact is one which could potentially be exploited by a remote attacker to get Log4j to execute arbitrary code either as the user the server is running as or root. It impacts Apache Log4j 2 versions 20 through 2141 Apache is nearly ubiquitous. A high severity vulnerability and proof of concept was released today for a vulnerability in Apache.
Log4J 2x version has got an option called message lookup substitution. A critical vulnerability has been discovered in Apache Log4j 2 an open source Java package used to enable logging in many popular applications and it can be exploited to. Today Dec10 2021 a new critical Log4j vulnerability was disclosed.
A previously unknown zero-day vulnerability in Log4j 2x has been reported on December 9 2021. The first-stage resource acts as a springboard to another attacker-controlled endpoint which serves Java code to be executed on the original victim. The vulnerability allows for remote code execution as the user running the application that utilizes the library.
What is Apache Log4J and why is this library is so popular. Log4j 2150 has been released which no longer has this vulnerability. As the POC published on GitHub points out when log4j logs an attacker-controlled string value it.
This vulnerability allows an attacker to execute code on a remote server. It does not have the potential to impact. Exploit proof-of-concept code is widely available and internet wide scanning suggests active exploitation.